By Jay Palter | June 8, 2023
Internet of Things (IoT) technology continues to disrupt both the consumer and enterprise sectors and as new use cases are found, its adoption is only expected to grow. That includes many powerful applications in physical security, access control, and operations management.
And yet many Internet of Things security risks remain.
The very network connections that drive the IoT are also its greatest liability, opening previously-secure physical infrastructure to remote network-based attacks. But with a little insight and careful planning, IoT security technology can be effectively deployed in any organization.
What is IoT?
The Internet of Things is the latest generation of physical infrastructure embedded with Internet connections. Think of security cameras that can email homeowners motion-detected video clips on their own. Or asset management lockers that notify supervisors when sensitive equipment isn’t returned at the end of a shift.
Why IoT System Security Matters
IoT technology is spreading fast. The research firm IoT Analytics estimated that 14.3 billion IoT devices were used worldwide in 2022. That figure is expected to grow to 29 billion by 2027.
The threats against them have increased too. In a few short years, IoT attacks have gone from solely a national intelligence agency tool to standard kit for hackers. In fact, one of the largest ‘denial of service’ attacks in Internet history and the single largest cyber-attack of 2016 was perpetrated by novice hackers targeting IoT security cameras, printers, and even baby monitors. Using a network of these infected devices, the attackers were able to disrupt Internet service for much of the eastern United States.
Today there are even publicly available IoT device search engines that let anyone, security professionals and hackers alike, find devices anywhere in the world. Internet of Things threats now target physical infrastructure. Attacks on physical infrastructure no longer necessarily come through the front or back door. Instead, they can now come from another hemisphere.
How Do IoT Security Solutions Work?
IoT technology is the glue that holds together modern, networked IoT security solutions. They connect to wider security and access control infrastructure in several important ways.
Sensors
IoT technology allows security systems to self-monitor and collect data about themselves. That is often performed over a wireless communication standard in security systems, like radio frequency identification (RFID). RFID is a short-range wireless standard most often used for computer-to-computer communication. One great thing about RFID Internet of Things sensors is that each tagged device has a unique identity in the security system so that you can track assets over their entire lifecycle in your organization.
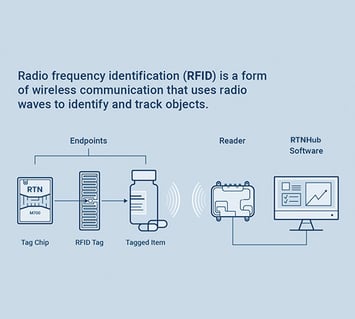
Computer Management
Data collected from the IoT sensor network feeds back to a central computer system. Data is stored for reporting and analysis. You can also configure the management system to trigger responses to events you specify. The management system can relay this information to human operators.
.jpeg?width=355&height=320&name=Blog-%2385_Inside_Banner_1200x1080_2%20(1).jpeg)
Controllers
Controller components take action in response to the management computer’s decisions. For example, in an IoT security solution could be the compartments in an asset management system that sends an alert to a supervisor if someone returns a kit with a missing component not read by the locker’s content surveillance system. Or it could be the locking slot in a key cabinet that won’t release a vehicle key if the previous user reported a serious mechanical fault.

Analytics: The Key Benefit of IoT Security Solutions
Analytics is the process of gathering, interpreting, and deriving meaningful insights from data to support decision-making. It involves using statistical analysis, data mining, predictive modeling, and machine learning techniques to discover actionable insights you might never notice through manual, human observation.
The greatest benefit of IoT security solutions is their data-gathering capabilities to support operational and strategic analytics. Leveraging IoT analytics from smart key, asset, and access control systems improves organizations in many ways.
Enhanced security
Analytics data from IoT sensors and smart security systems help organizations monitor their physical security in real-time. By analyzing access patterns, administrators can detect potential security problems, such as repeated unauthorized access attempts by the same individual or personnel on the same shift, incorrectly logged equipment returns, or access at irregular hours. These data-fueled insights empower business and security personnel to protect your valuable assets better and take immediate action in response to security incidents.
Improved operational efficiency
Security system analytics provide valuable insights into how people use your equipment and facilities. Those insights can help make business operations more efficient. By analyzing usage patterns on an asset management system, you might learn how to streamline cumbersome business processes using stored assets. You can adjust future procurement budgets after analyzing current cycle equipment use. And you can ensure that the right resources are available daily.
Detailed audit and compliance records
Analytics support your creation of comprehensive audit trails and compliance reports. Organizations can better demonstrate compliance with government regulations, industrial IoT security standards, and internal policies by tracking transactions and access events such as time stamps, transaction locations, and user identities.
Better support for Lean Management
Since analytics provide organizations with valuable data on the effectiveness of their security systems, they’re an excellent platform to support business methodologies like Lean. By analyzing metrics, such as transaction times, reported fault codes, and overdue returns, organizations can identify processes to improve and optimize.
Unlock the Secrets of Building a World-Class Physical Security Program.
Read our guide: Physical Security 101: How to Start Building a World-Class Security Program.
IoT Security Issues to Beware Of
IoT technology is powerful, but it overlaps our physical and network security environments in ways that can be exploited. This is particularly important to consider as businesses deploy more and more IoT systems within their physical security infrastructure. Deployed improperly, these security systems can become vulnerabilities themselves.
If your business uses or plans to use IoT systems, it pays to know the tactics attackers might use to target them.
Skimming

A hacker can position a ‘skimming’ device near one of your IoT assets to wirelessly copy data. This could include copying smart card or fob access credentials or sensitive data directly off IoT security cameras, printers, or other infrastructure.
Possible Solution:
Attackers and their tools need to be separated from your assets. For example, you can require guests in your facility to deposit unapproved equipment beyond your perimeters in secure asset lockers. Or adjust access control measures at your perimeters.
Eavesdropping
Eavesdropping attacks to intercept sensitive communication used to only take place over the Internet. Now attackers can position scanning devices physically next to IoT infrastructure on-site to do the same. This could include lifting access control data at your perimeter—or sensitive data directly from wirelessly-enabled data mobile devices or laptops.
Possible Solution:
Controlling the movement of assets and people alike is key here. For example, a real-time indoor positioning system could track access keys, assets, or personnel within your facility, depending on your specific needs. Or secure your idle electronics in asset lockers.
Relay Attacks

IoT technology enables organized teams of hackers to carry out sophisticated relay attacks. For example, if an employee is off-site with their access card or fob, one attacker can skim their credential data. Then, a second attacker on-site at your facility can receive that data and impersonate that employee using a dummy broadcast IoT device to bypass your access control or asset management systems.
Possible Solution:
For particularly sensitive assets or keys that can never be exposed to such a threat, an exit alert system could notify security personnel to respond to assets approaching your perimeters.
Lateral Network Attacks

A lateral attack is when a hacker first comprises a less important but vulnerable device on a network—for example, an IoT air quality sensor. Then, they use their access to that device to force their way laterally, across your network, into another more sensitive or valuable system. They repeat this process undetected until they’ve comprised a valuable target, like a server with employee data or trade secrets.
Possible Solution:
Improve your edge security, or control over devices on the edge of your network. IoT sensors commonly live at the edge on purpose to intersect with real-world systems and generate more valuable data. That placement makes them important but also vulnerable. Security teams should conduct regular software and hardware updates on your edge devices as often as on core systems.
IoT is Driving Security Convergence
If there weren’t enough indicators already, IoT convergence has become a necessary security approach, as IoT technology has literally converged our physical and network infrastructure.
Going hand-in-hand with such a converged program comes a need for increased communication and security education throughout your organization. IoT technology can turn any employee’s mobile device into a potential threat. Therefore, your organization must know and participate in your security efforts.
And when in doubt, get expert assistance evaluating and deploying new systems. IoT technology is powerful but complex. Making sure it’s used both effectively and securely within your organization can require insight from dedicated experts.
Ready to enhance the security of your IoT infrastructure?
Schedule a demo today and see how our IoT security solutions can protect your organization.
Subscribe to our blog

Jay Palter
Vice President of Marketing & Partnerships




